How to Protect Your Site From Dangerous WordPress Security Issues
WordPress is one of the most popular platforms around. From blogs to web pages, the software packs a punch for hardcore developers and newbies alike. But then there are the code vulnerabilities. Fortunately, there are ways to minimize these security issues and create beautiful and functional pages that people can safely visit again and again.
The following tips should help overcome the more common WordPress vulnerabilities.
1. Keep Your Plugins Up to Date
Plugins are perhaps the most exciting thing about WordPress. With them, your site can offer features and functions perhaps to the limit of your imagination. So functional that, in the hands of a skilled website builder, it’s possible to use the right combination of plugins to create pages that perform much like an app.
The thing to remember is that plugins come with vulnerabilities which are usually not known at the time of release. It’s only after hackers push and prod the code until they find a weakness and then develop malware that the problems emerge. Typically, fixes are produced and included in the next release to compensate and protect site owners.
Having said this, it’s in your best interest to be on the lookout for new versions of plugins you use. More to the point, you should replace the older versions as soon as more recent iterations are available. Even if you’ve not noticed problems, make the updates.
2. Only Use Plugins From a Trusted Source
WordPress is not the only place to find compatible plugins. They are also developed and released by other parties for free or purchase off platform. Many plugins you find in this manner are stable and relatively free of vulnerabilities but others are built with malware included specifically to penetrate and infect any system it is installed in.
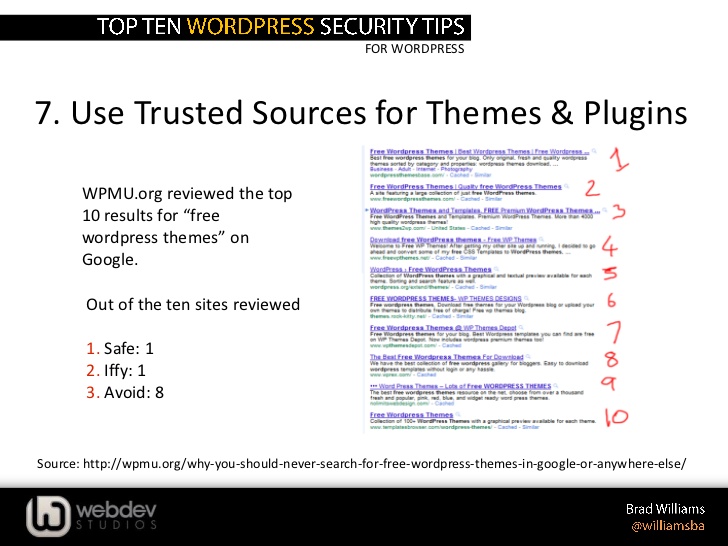
Your best bet is to only use plugins from a trusted source. Trusted means that the developer takes the same precautions that come with the creation of WordPress branded plugins. The developer should also actively monitor the device in the event security issues are uncovered and need to be resolved in the form of a new version.
If you don’t see evidence that a plugin creator is consistently spotting and correcting vulnerabilities, don’t trust it and certainly don’t install it. If you already have, immediately uninstall and remove that plugin from your website.
3. Get Rid of Plugins You No Longer Use
Do you have plugins installed that are no longer used? If so, ditch them immediately. There are a few reasons we say this:
- Old plugins that you never use are old versions with old protections; they may not stop viruses or malware from infecting your site.
- They take up space you could use for something more practical.
- It’s easier to manage your pages when you only have plugins installed that are needed.
Make it a point to review your plugins at least once a quarter. Maybe even monthly if you don’t have anything better to do. Find a few you don’t use any more? Get rid of them. Remember that if you need them in the future, it’s easy enough to re-install the most recent release.
4. Protect Your Site From SQL Injection and URL Hacking
Structured Query Language is important, but injections of SQL by an attacker can wreak havoc on your pages. They can alter, add, or replace the content on those pages and do quite a bit of damage. Hacking your Uniform Resource Locator (URL) makes it possible to alter the address of your pages and redirect readers to pages created by a hacker. Not only do you lose business, but your reputation could take a serious hit.
The right type of WP Config tool helps to prevent both these possible issues. As with all of the tools, make sure you use the latest generation.
5. Change the Default Prefix For Your Site’s Database
Upon installation, WordPress creates a default prefix for your database tables. It’s a good idea to take the time to customize those prefixes since a common hacker trick is to use specialized software to identify and alter them, then use SQL injections to take over.
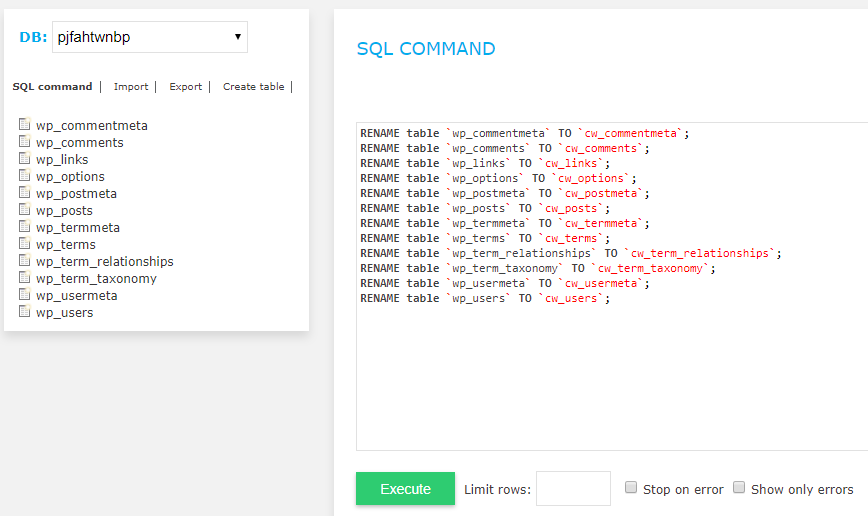
Changing database prefixes is not that difficult. In fact, it can be done fairly quickly. See it as one more way to ensure your hard work isn’t corrupted or used without your permission.
6. Use Two-Factor Authentication
Two-factor authentication has become a big deal in recent years. Essentially it’s a two-step login process that, in addition to the usual username and password, requires an additional code sent to you by phone or some other alternate means.
This process adds an extra step but makes it more difficult for unauthorized parties to gain access since they likely won’t be able to hack your computer and phone simultaneously.
7. Don’t Go Online Without a Virtual Private Network (VPN)
If this is your first exposure to the idea, personalized encryption tools, in the form of a VPN, have brought intelligence agency-level privacy and anonymity to the masses. This software, once installed, creates an encrypted connection (some like to think of it as a tunnel) every time you go online, even if you’re knocking back caffeine down at the local coffee shop using public Wi-Fi.
A VPN, used in conjunction with other open source privacy tools, is at least an attempt at a solution to the outbreak of hacking, data breaching, and government spying that is sweeping the internet with no letup in sight. A VPN runs in conjunction with your ISP service and should cost no more than $7 to $15 a month.
8. Go With Dedicated Rather than Shared Hosting
Shared hosting is fine and may work well for many people but business sites and especially if you collect customer data (gotta be aware of the new GDPR regulations), you might consider the extra expense of dedicated hosting.
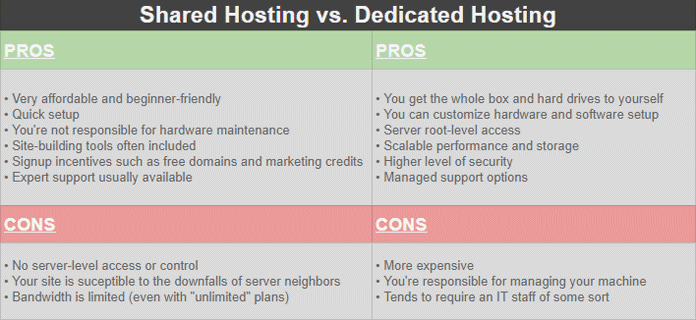
Most experts agree that the dedicated hosting environment offers tighter security, which is a good thing.
8. Monitor and Update Administrative Privileges Regularly
One of the more common tasks overlooked in WordPress is updating administrative privileges, which needs more attention than simply deleting privileges when an employee leaves the business.
You should also update privileges around situations like promotions, changes in work assignments, and anything else that could leave an employee with access to data he or she no longer needs.
Old and unused privileges increase the odds of information disclosures if an infection is able to find a way to exploit them. Make sure administration level rights are limited to active employees who actually need access to that level of control.
Final Thought
Remember that WordPress continues to develop and release security tools that you can put to good use. Review those resources as they become available. One or more of them may be just what you need to make your security even better. And always…ALWAYS…update the main installation any time you are prompted to do so in the dashboard area. Hackers are always trying to uncover new methods of entry and this is how you stop them.
